Other recent blogs



Let's talk
Reach out, we'd love to hear from you!
With the introduction of the NetWeaver Process Orchestration B2B add-on, SAP is covering all aspects of Application to Application (A2A) and Business to Business (B2B) integration, eliminating the need to deploy any third-party adapters. This B2B add-on is included as part of the standard license for Process Orchestration (Single Stack) 7.31 or higher. On the other hand, for Process Integration (Dual Stack) it might require additional licensing costs.
New Features in SAP PI
- File adapter that supports the transfer of large (unlimited file size) binary files
- Sender HTTP adapter that supports HTTP GET method
- Publish and subscribe via Java Message Service (JMS) adapter
- In addition to FTP and FTPS; File adapter supports Secure File Transfer Protocol (SFTP) as well
- B2B adapters like Applicability Statement 2 (AS2), Odette File Transfer Protocol (OFTP), X.400 and support for Electronic Data Interchange For Administration, Commerce, and Transport (EDIFACT), ANSI X.12, VDA, TRADACOMS, and ODETTE
- Built-in support for Pretty Good Privacy (PGP) encryption and decryption
- Ability to ping adapters and check their status (Active/Inactive/Stopped)
- Blacklisting of error messages. If a message runs into error several times, it can be flagged and moved to another queue. This will prevent messages from getting stuck in queues and avoid blocking other messages
- Enhanced message search capabilities based on values from payload and adapter-specific message attributes, for e.g. searching an IDOC based on “Customer Name” or “Customer Number,” etc.
The B2B and EDI Capabilities of SAP PI
- Message-level encryption for secure message content
- Transport level encryption for secure message content
- Data stream encryption via Secure Sockets Layer (HTTPS)
- Security based on the Web Service standard (WS-Security)
- AS2 support
- Support for EDIFACT, ANSI X12, TRADACOM, SWIFT etc.
Configuring B2B Adapters in PI – AS2
All the B2B adapters can be configured in the integration repository, just like any other out-of-the-box adapters (e.g. File, SOAP, JDBC, IDOC, etc.).
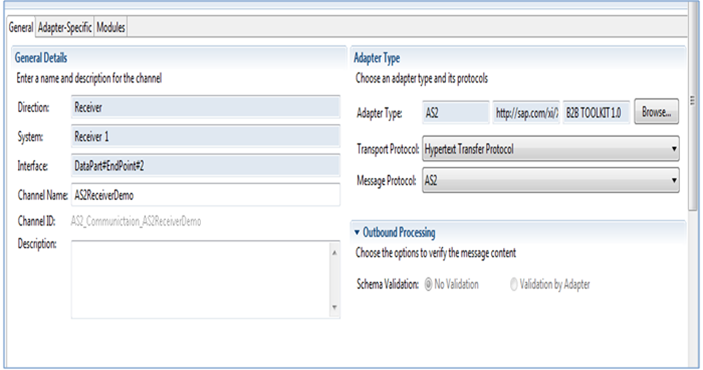
The PGP Capabilities of SAP PI
Encryption
- Encrypt Only
Use the public key provided by the partner to do encryption. Along with the public key, you can also specify the encryption algorithm. The SAP standard module supports the following algorithms for encryption: AES_128, AES_192, AES_256, BLOWFISH, CAST5, DES, 3DES, and TWOFISH.
- Sign and Encrypt
In this case, along with the public key, you also need your own private key and its passphrase to sign the message. The following algorithms can be used to sign messages MD5, RIPEMD160, SHA1, SHA224, SHA256, SHA384, and SHA512.
- Compression
This is optional and allows you to define necessary compression that needs to be carried out on the message, reducing message size. The supported compressions are ZIP, ZLIB, and BZIP2
Decryption
- Decrypt Only
In case of decryption, you need to use your private key and its passphrase. There is no need to exclusively specify the algorithm, as it will be automatically detected by the module.
- Decrypt and Verify
To verify sender’s signature, partner’s public key along with your private key and passphrase must be provided. There is no need to provide any algorithm information.
Configuring PGP Adapters in SAP PI
You can secure the transmission of your business data over the Internet by configuring communication channels with the PGP module. The cryptographic algorithm of the PGP module encrypts sensitive data and transmits it securely so that it cannot be read by anyone except the intended recipient.
The release of B2B, EDI, and PGP capabilities has enabled the use of SAP PI/PO for all your internal (Application to Application) and external (Business to Business) integration needs, eliminating the need to deploy any third party adapters.



